Security Risk Management Course
Security Risk Management Course - Master the fundamental principles and concepts of security risk assessment and optimal security risk management in information security based on iso/iec 27005. Learn to prioritize threats, select appropriate safeguards, and ensure regulatory compliance. This course takes a deeper dive into concepts introduced in the first course, with an emphasis on recognizing the focus of the cissp eight security domains, steps of risk management, security frameworks and controls (e.g., nist, cia triad, owasp), as well as common security threats, risks, and vulnerabilities. Transform you career with coursera's online risk management courses. In this course, you will learn about the general information security risk management framework and its practices and how to identify and model information security risks and apply both qualitative and quantitative risk assessment methods. This course will equip you with the knowledge and skills needed to identify, evaluate, and manage it risks in alignment with business goals. This track prepares you to apply security analytics, risk assessment and policy management to protecting health information. Complete all three courses and assessments to earn the risk management certificate and a credly digital badge to display on social media and your. Learning objectives be familiar with various information security frameworks, security policies, and the risk management lifecycle. In this specialization, you will learn how to define cybersecurity risk and discuss the threats that create it while you also learn to describe the role of cybersecurity management in the management of cybersecurity risk. Risk management is a continuing process that identifies, analyzes, evaluates, and addresses exposures and monitors risk. Control selection, implementation and assessment; This involves evaluating the security needs for an event and if a crisis should occur, having a crisis management team in place to manage it. System and common control authorizations; Master the fundamental principles and concepts of security risk assessment and optimal security risk management in information security based on iso/iec 27005. By the end of the program, you will be equipped for occupations such as health information security director, health it project manager or cybersecurity analyst for medical records. This leaves cisos in a challenging position. Learn how to identify, assess, and manage security threats and risks, developing strategies to mitigate potential vulnerabilities and enhance security resilience. The risk management framework (rmf) provides a disciplined, structured and flexible process for managing security and privacy risk. In this specialization, you will learn how to define cybersecurity risk and discuss the threats that create it while you also learn to describe the role of cybersecurity management in the management of cybersecurity risk. In today’s interconnected digital world, effective risk assessment and management are crucial for maintaining a robust cybersecurity posture. This leaves cisos in a challenging position. Transform you career with coursera's online risk management courses. Cybersecurity affects everyone, including in the delivery of basic products and services. This masterclass combines the content of our four most popular and practical courses—fundamentals of. A security and risk management course teaches you the principles and practices involved in protecting an organization from security threats and risks. Master the fundamental principles and concepts of security risk assessment and optimal security risk management in information security based on iso/iec 27005. Learn how to identify, assess, and manage security threats and risks, developing strategies to mitigate potential. System and common control authorizations; In this course, you will learn about the general information security risk management framework and its practices and how to identify and model information security risks and apply both qualitative and quantitative risk assessment methods. It covers areas such as risk assessment, crisis management, and compliance with legal and regulatory standards. This involves evaluating the. Learn to prioritize threats, select appropriate safeguards, and ensure regulatory compliance. Risk management is a continuing process that identifies, analyzes, evaluates, and addresses exposures and monitors risk. It includes information security categorization; In this specialization, you will learn how to define cybersecurity risk and discuss the threats that create it while you also learn to describe the role of cybersecurity. Learn how to identify, assess, and manage security threats and risks, developing strategies to mitigate potential vulnerabilities and enhance security resilience. System and common control authorizations; It includes information security categorization; This course will equip you with the knowledge and skills needed to identify, evaluate, and manage it risks in alignment with business goals. In this specialization, you will learn. It covers areas such as risk assessment, crisis management, and compliance with legal and regulatory standards. In this specialization, you will learn how to define cybersecurity risk and discuss the threats that create it while you also learn to describe the role of cybersecurity management in the management of cybersecurity risk. Learning objectives be familiar with various information security frameworks,. This course will equip you with the knowledge and skills needed to identify, evaluate, and manage it risks in alignment with business goals. Learn to prioritize threats, select appropriate safeguards, and ensure regulatory compliance. It includes information security categorization; Learn how to identify, assess, and manage security threats and risks, developing strategies to mitigate potential vulnerabilities and enhance security resilience.. System and common control authorizations; A security and risk management course teaches you the principles and practices involved in protecting an organization from security threats and risks. This involves evaluating the security needs for an event and if a crisis should occur, having a crisis management team in place to manage it. It covers areas such as risk assessment, crisis. Control selection, implementation and assessment; Risk management plays a crucial security role at organizations around the globe. System and common control authorizations; This course will equip you with the knowledge and skills needed to identify, evaluate, and manage it risks in alignment with business goals. However, security and risk management (srm) leaders remain accountable for helping the enterprise balance the. The journey begins with a strong foundation in security concepts, governance principles, and legal frameworks, including iso and nist. In this course, you will learn about the general information security risk management framework and its practices and how to identify and model information security risks and apply both qualitative and quantitative risk assessment methods. This track prepares you to apply. This course takes a deeper dive into concepts introduced in the first course, with an emphasis on recognizing the focus of the cissp eight security domains, steps of risk management, security frameworks and controls (e.g., nist, cia triad, owasp), as well as common security threats, risks, and vulnerabilities. Control selection, implementation and assessment; Learn to prioritize threats, select appropriate safeguards, and ensure regulatory compliance. Risk management is a continuing process that identifies, analyzes, evaluates, and addresses exposures and monitors risk. It covers areas such as risk assessment, crisis management, and compliance with legal and regulatory standards. This cissp | domain 1: Information security and risk management course will cover various information security frameworks, security policies, and the risk management lifecycle. Complete all three courses and assessments to earn the risk management certificate and a credly digital badge to display on social media and your. By the end of the program, you will be equipped for occupations such as health information security director, health it project manager or cybersecurity analyst for medical records. Learn how to identify, assess, and manage security threats and risks, developing strategies to mitigate potential vulnerabilities and enhance security resilience. This course will equip you with the knowledge and skills needed to identify, evaluate, and manage it risks in alignment with business goals. However, security and risk management (srm) leaders remain accountable for helping the enterprise balance the risks and benefits of emerging technology. In this specialization, you will learn how to define cybersecurity risk and discuss the threats that create it while you also learn to describe the role of cybersecurity management in the management of cybersecurity risk. In today’s interconnected digital world, effective risk assessment and management are crucial for maintaining a robust cybersecurity posture. In this course, you’ll dive deep into the essential components of security and risk management, aligned with the latest cissp curriculum. A security and risk management course teaches you the principles and practices involved in protecting an organization from security threats and risks.Security Risk Management Masterclass
Diploma of Security and Risk Management CPP50619 Paragon training
Security Training Courses Handgun Training Shield Corporate Security
Security and Risk Management Course
Security Risk Management Online Course & Certification
TRAINING SECURITY RISK MANAGEMENT Mitra Solusi Training
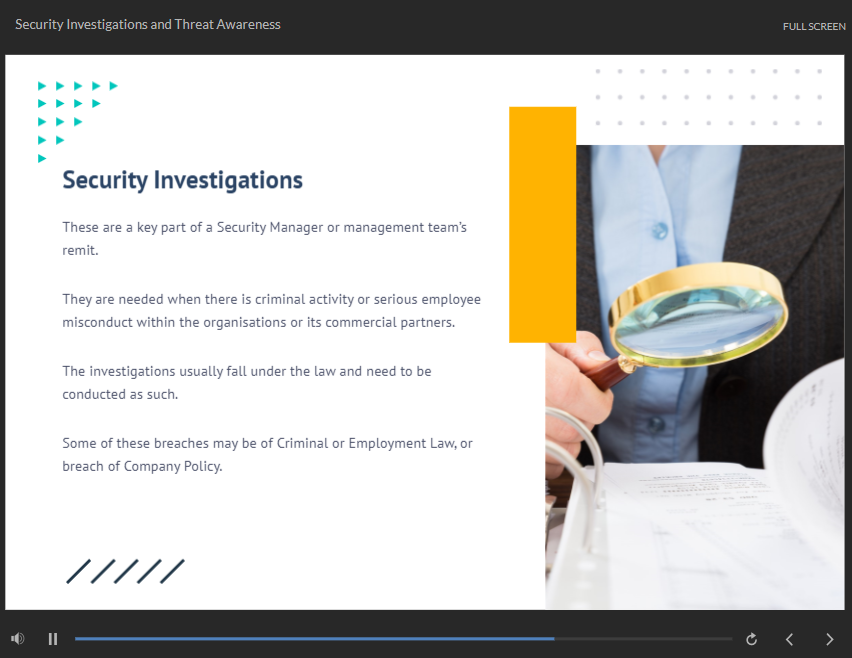
Aboutsecurityrisk
Information Security Risk Management Course Three O
TRAINING SECURITY RISK MANAGEMENT Mitra Solusi Training
Security and Risk Management Question CISSP Course
This Involves Evaluating The Security Needs For An Event And If A Crisis Should Occur, Having A Crisis Management Team In Place To Manage It.
System And Common Control Authorizations;
Gain Skills In Cybersecurity And Risk Management.
Master The Fundamental Principles And Concepts Of Security Risk Assessment And Optimal Security Risk Management In Information Security Based On Iso/Iec 27005.
Related Post: